Certificates and different PKIs in DOCSIS 3.1


Privacy is an integral and important part of DOCSIS because of the shared medium over which it operates (the HFC network). Since version 1.1, the authentication of cable modems is done using a chain of X.509 certificates (PKI infrastructure). This blog post explains the history of the different PKI infrastructures and how it will look like in DOCSIS 3.1.
Encrypting the data
DOCSIS uses a shared medium. To prevent eavesdropping, privacy was an important part of the specification from the very start (DOCSIS 1.0).
Since every single packet on the MAC layer needs to be encrypted/decrypted, speed of operation is important. Therefore symmetric keying is used for encryption, using DES or AES (introduced in DOCSIS 3.0) as encryption algorithms.
The negotiation of the symmetric keying material is done using a unique public/private keypair (RSA) installed on each modem. This not only improves the overall security, it’s also essential for scalable distribution of the symmetric keying material, which is periodically refreshed using that public key. This is a typical trade-off between speed and security.
The entire mechanism of encryption and key negotiation is called the Baseline Privacy Interface (BPI).
From BPI to BPI+
While sufficient for data protection, BPI does not provide any authentication of the cable modems. To tackle this, a chain of X.509 certificates was introduced in DOCSIS 1.1. Such a chain of certificates allows the authentication of the modem’s public key. This is basically the same mechanism as is used in your browser for websites with a green padlock icon, indicating that the HTTPS session is properly secured and authenticated. For your browser, there are multiple root certificates (on top of the trust chain) and you can add others. For DOCSIS, a single root certificate was created by CableLabs.
Trusted manufacturers get their certificate signed by the CableLabs root certificate authority and can then in turn sign their own cable modem device certificates.
The certificate chain looks as follows:
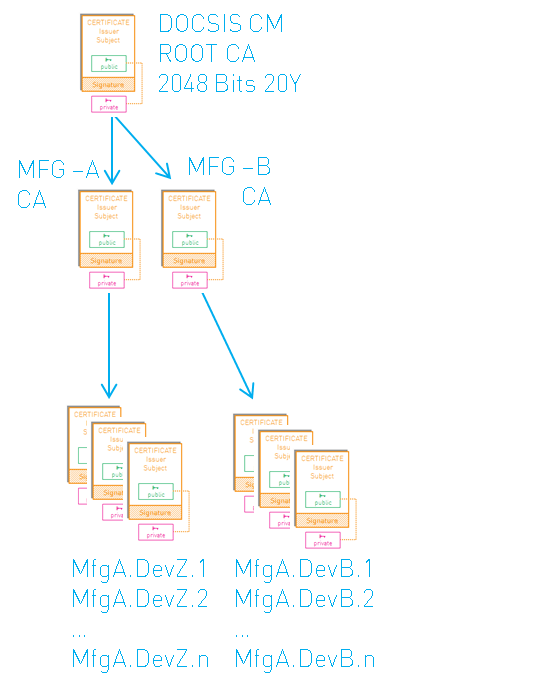
The root certificate is installed into the CMTS. A modem has its private key and the corresponding device certificate, as well as the manufacturer certificate, installed at production time. When a modem comes online, it sends its device and manufacturer certificate to the CMTS, which verifies the authenticity of the modem by chaining these certificates to its installed root certificate.
The EuroDOCSIS PKI
The European variant of DOCSIS (EuroDOCSIS) came with its own PKI and chain of certificates, specified in the EuroDOCSIS-BPI+requirements document. This PKI is very similar to the CableLabs one, except that the root certificate is managed by Excentis on behalf of the European Cable Operators.
The EuroDOCSIS certificate chain looks as follows:
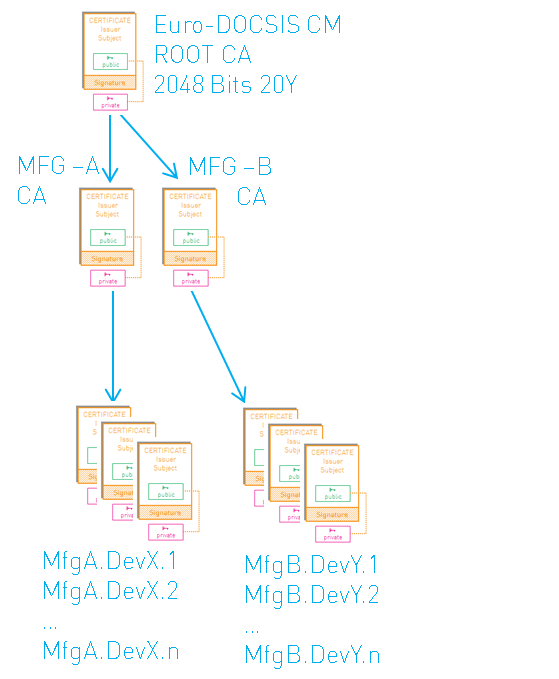
A CMTS that is capable of operating in both DOCSIS and EuroDOCSIS mode is required to have both root certificates installed.
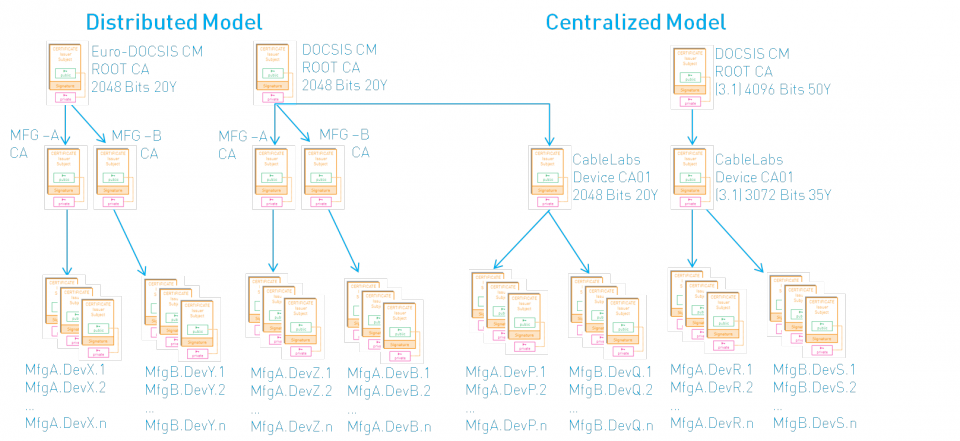
Distributed versus centralized model
In the later versions of the BPI+ specification (I11 and later) an alternative to the original DOCSIS PKI was proposed, where all the modem certificates were signed by a CableLabs certificate. A single CableLabs certificate (the Device CA) now takes the role of the different Manufacturer CAs.
This is referred to as the centralized model. The original model where the manufacturers signed their own modem certificates was called the distributed model.
The centralized model looks as follows:
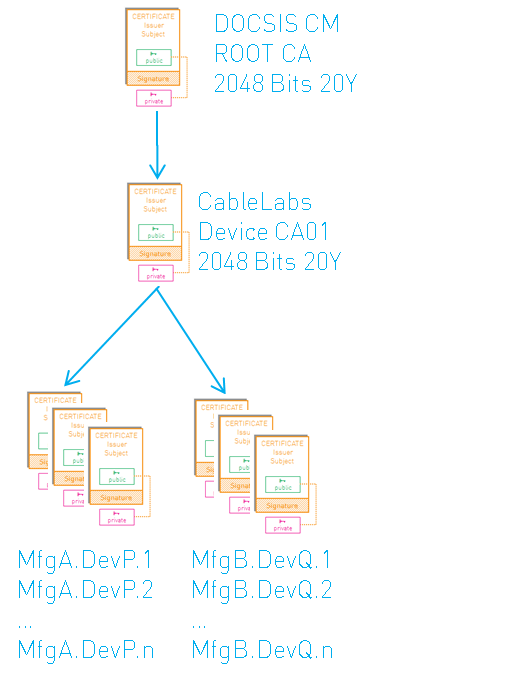
For the CMTS it makes no difference, since the modems send their manufacturer certificate to the CMTS each time they come online. Now the Device CA certificate is sent instead of the manufacturer certificate.
Note that there is no centralized version of the EuroDOCSIS PKI.
A new PKI in DOCSIS 3.1
To provide stronger cryptography, a new centralized PKI was introduced in DOCSIS 3.1. This PKI is very similar to the centralized version of the BPI+ PKI, except for the increased key sizes:
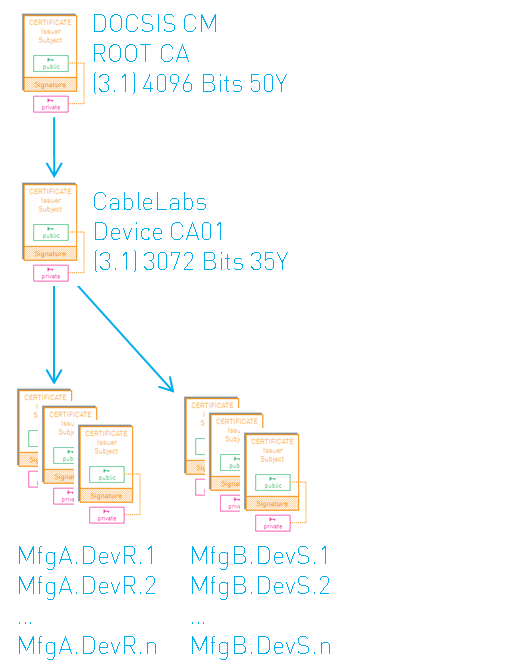
Since there is no European or other variant in 3.1, this is the only PKI for all DOCSIS 3.1 deployments. One root certificate to rule them all, so to speak.
Putting the pieces together
Great, that simplifies things. Or doesn’t it?
Well, not really. There is still something called “Backwards Compatibility”. Every 3.1 CMTS needs to be able to accommodate pre-3.1 CMs and every 3.1 CM must be able to operate on a pre-3.1 CMTS.
A 3.1 Cable Modem needs to have two device and manufacturer certificates installed: one set from the new 3.1 PKI for use on a 3.1 CMTS and one from the old (either distributed or centralized) PKI for pre-3.1 CMTSes. For EuroDOCSIS the certificates from the old PKI need to be the EuroDOCSIS ones.
A 3.1 CMTS needs to have the new 3.1 root certificate installed and —depending on DOCSIS or EuroDOCSIS legacy mode support— one or both of the legacy root certificates.
Putting the pieces together, the following image gives an overview of all the PKIs that are in place in a DOCSIS 3.1 environment:
Conclusion
While DOCSIS 3.1 introduced a single PKI chain for all modems, backwards compatibility makes things more complicated than that.
And that’s excluding the test chains that are needed for the Security ATP testing.
We also didn’t mention that the same PKI is also used for the secure software download of the modems — but that’s another story, covered in a blog post titled Secure Software Download in DOCSIS 3.1.
More information
For learning more on DOCSIS 3.1: among other courses, we have a 2-day training course “DOCSIS 3.1” that takes an in-depth look at the changes introduced by DOCSIS 3.1.























Thank you for the detailed explanation.
BTW, the MfgA.DevB.x in diagram under ‘From BPI to BPI+’ and ‘Putting the pieces together’ shall be MfgB.DevB.x
Thanks Roy, and well spotted! 🙂